Take your hands off my files
A few days ago, an attacker managed to publish malicious updates to two popular npm packages. On installation, these packages uploaded the user’s npm credentials to pastebin.com.
This incident serves as a good reminder on how much trust we put in each and every application we run on our machines.
I’m actually surprised the malicious npm packages “only” uploaded the user’s npm credentials. Who’s to stop them from uploading your ~/.ssh? Your cookies? Your emails? Your ~/Documents? Rest assured, your drivers are safe.
After having my paranoia levels heightened a few years ago, I was relieved when Jonathan Zdziarski released Little Flocker since it solved one of my main security worries. In short, Little Flocker is to your files what Little Snitch1 is to your network. For example:
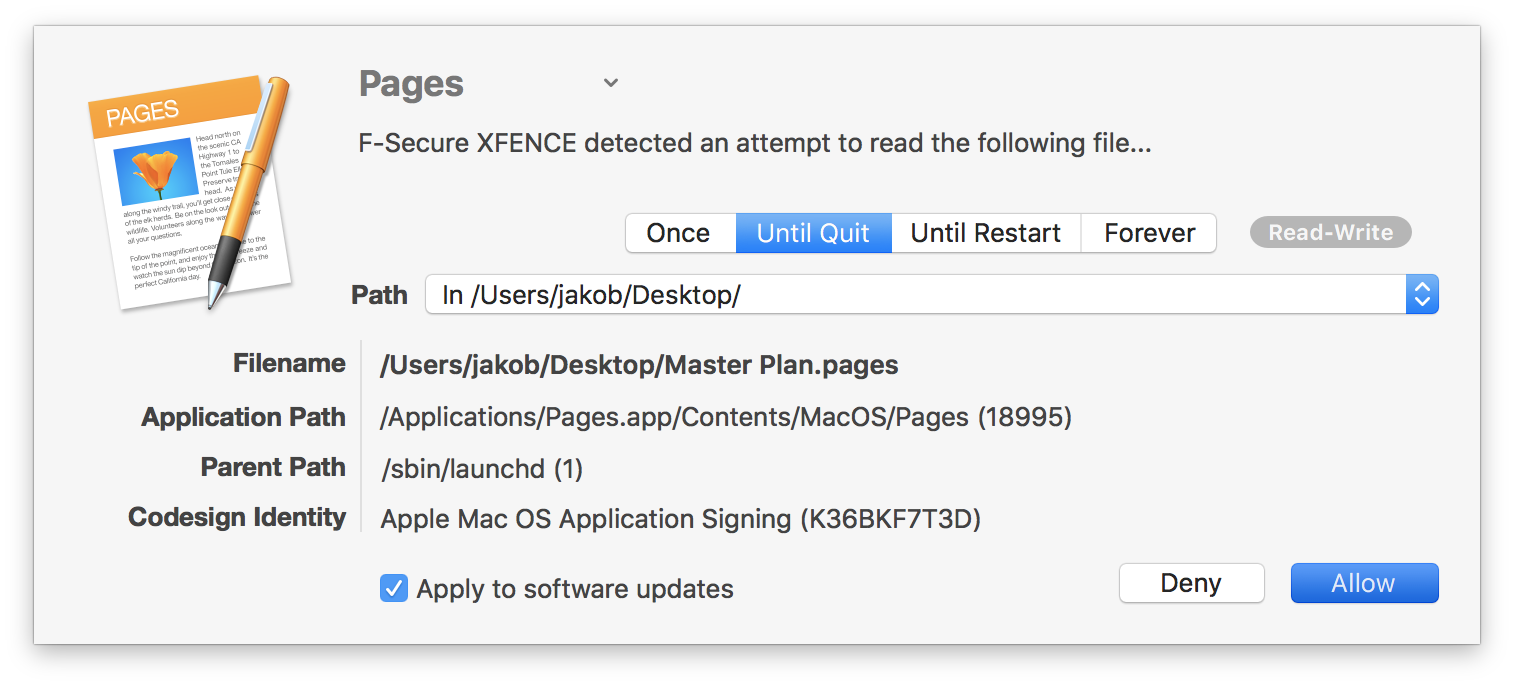
After Zdziarski joined Apple’s Security Engineering and Architecture team in March 2017, Little Flocker was sold to F‑Secure and rebranded as F‑Secure XFENCE. Sadly, development has mostly stagnated since then.
On the bright side, Zdziarski’s efforts inside Apple seem to bear fruit in macOS Mojave: Accessing specific data, such as your mail database, message history, and system cookies, will require user consent in the security and privacy preference pane.
All in all, I’m not really happy with the status quo. We could all just be one npm install, one curl | bash, or one brew install away of having our data being taken ransom. macOS could really learn a lot here from iOS’s security architecture.
-
For a while, I was actually using Little Snitch. However, Little Flocker made me realize that I don’t really care about network requests but the personal data on my device. ↩